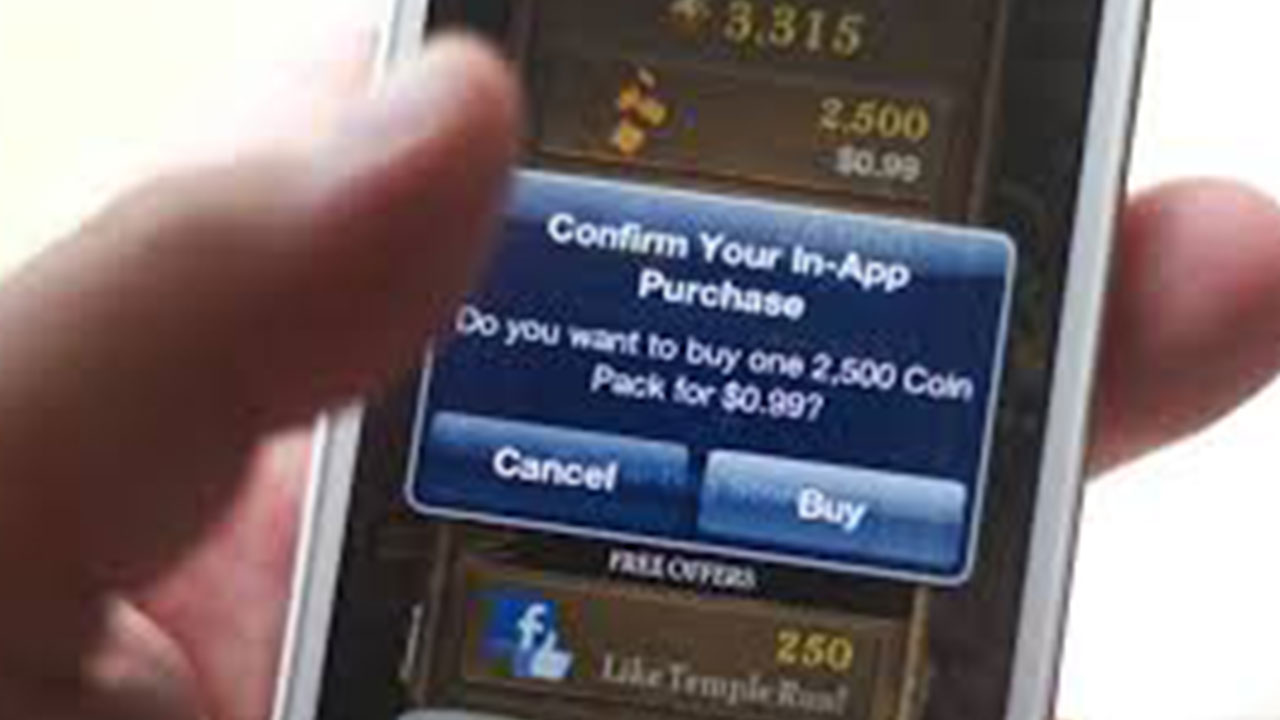
Apple’s In-App Purchase program for iOS has been hacked by a Russian developer who discovered a way for iPhone, iPad and iPod touch users to circumvent the payment process, essentially stealing in-app content.
This news comes on the back of revelations that the first Trojan Horse Virus was found within an approved app on the Apple App Store earlier this month.
“The security of the App Store is incredibly important to us and the developer community,” Apple representative Natalie Harrison, told The Loop. “We take reports of fraudulent activity very seriously and we are investigating.”
The “in-app proxy” method doesn’t require the phone to be jailbroken and works on all devices running iOS 3.0 to 6.0 with the developer claiming that completed by novices in just three steps!
While the technique appears to have a solid programming foundation utilising certificates and re-routed DNS servers to trick iTunes into allowing all purchases to be approved, the developer is using a website to handle the back-end processing and this site requires users to provide, what could effectively be, complete, open access to their phones and they are suggestions that he could also be building up a massive stockpile of users iTunes login credentials and unique data that identifies your specific device.
Now that this is out in the open you can expect that Apple will be working feverishly on finding a solution and the true effect of this hack will not be understood until it is determined if the solution is something that Apple can resolve with an iOS update or if there will be a need for individual apps to be updated to patch this security flaw.
There is a detailed overview of the hack’s functionality covered in this article on ZDnet.
9to5mac.com was one of the first to break this news as a warning to the Apple developer community and is updating their story as new news comes to hand and most recently reported that “TNW spoke with Alexey V. Borodin, the developer of the hack, who claimed apps using Apple’s method of validating receipts mentioned above are not safe. According to Borodin, only developers using their own servers to verify in-app purchases are able to dodge the hack.
This news would suggest that there is a likelihood that the solution to this problem may lay in the hands of the iOS developers and if that is the case then implementation of a solution could become a very costly exercise both in patching the security flaw itself and in lost revenue from in-app purchases until then.
Update 17 July: Great post on the Guardian.co.uk blog that further explains how this hack works and also raises a great point about lost payments for developers, “It is unclear though whether Apple or developers will be able to detect – or take action – against users who have taken advantage of the system, nor whether the company will refund developers who have lost payments as a result of the hack.”